-
10 basic cyber security rules for your business

Last week I gave a cyber security awareness session for the EuroCham office staff. During my preparation for this session, I saw that all the experts are saying a few basic but important things. To understand what kind of behavior is harmful for an organization, you have to understand what kind of risks are out…
-
Network Security Groups
Need a L4 ACL to control permitted flows? Create Network Security Groups (NSGs) using Application Security Groups (ASGs). Lab Overview In this lab, we will see how to create network security groups. Network Security Groups enable restricting flows at a subnet or at a virtual machine’s network interface level. We will create rules and apply…
-
Top 7 Data Security Tools and Technology

Due to the increase in modern technologies, and digital databases among organizations, the importance of data security is also increasing. Data security is mainly a set of procedures that are used to safeguard important information. Hence it is necessary to maintain the security of the data among the organizations. Data can be protected from internal or…
-
VRF in Networking: Virtual Routing and Forwarding
In networking, managing traffic is crucial for delivering high-quality services. One technology that plays a vital role in achieving this is Virtual Routing and Forwarding (VRF). VRF in networking allows multiple virtual routing tables to coexist within the same physical router, enabling service providers to offer tailored solutions for their clients. This blog aims to provide…
-
How do Solana validators secure the network?
Solana validators play a crucial role in securing the network by participating in consensus, validating transactions, and ensuring the overall integrity of the blockchain. Solana’s blockchain is unique in its combination of a Proof of Stake (PoS) system with a novel mechanism called Proof of History (PoH). Together, these technologies allow Solana to achieve high-speed…
-
Unlocking the Power of Digital Signatures: A Comprehensive Guide

Everything you need to know about Paperless Signatures The digital revolution is ever-changing and signatures and document verification haven’t been left untouched. Today, the traditional practice of signing documents with a pen is slowly declining and it is giving way to a more efficient, secure, and environmentally friendly method – the digital signature. In this…
-
What is Digital Citizenship and Why It Is Important
The idea of “digital citizenship” has grown in importance in the globally connected world of today. With the advancement of digital technologies merging with our everyday lives, it is pivotal to recognize what it implies to be an ethical digital citizen. In this article, we discover what is a digital citizen, including its significance, elements,…
-
Digital Security Act
Key Elements: There is provision for a digital forensic lab to be created for the analysis of digital matters; along with a digital forensic agency which will oversee all digital matters and a computer emergency response team that will be responsible for cyber attacks and ensure that critical information remains secure. Key details include: 27)…
-
Access Level
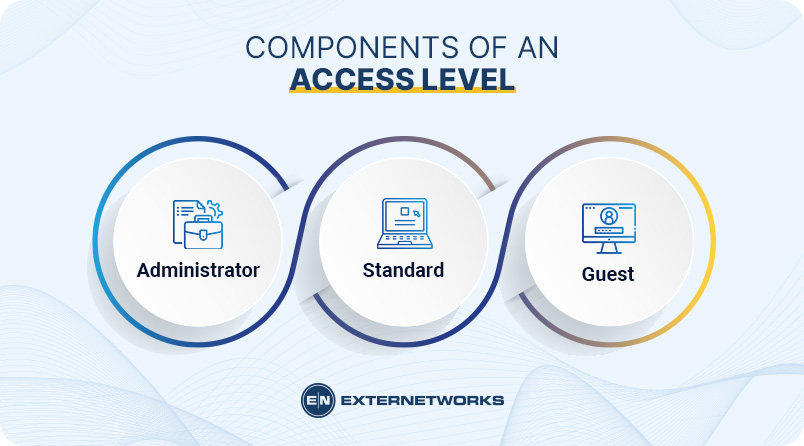
Access levels are a way for organizations to control who has access to information or resources. They are also known as security labels, permissions, roles, rights, or privileges. Access levels are often used to determine whether someone should be able to view certain documents or perform certain tasks. For example, they might allow employees to…
-
Security 101: Detecting and Protecting Shadow IT
Security is one of the most important aspects of your business in the modern world. After all, with so many ways for your company to become vulnerable, being aware of all of the security risks that your business might face is vital to be able to prepare and prevent a catastrophe. One of the most…

+91-133-436-7880




